
PDF Publication Title:
Text from PDF Page: 004
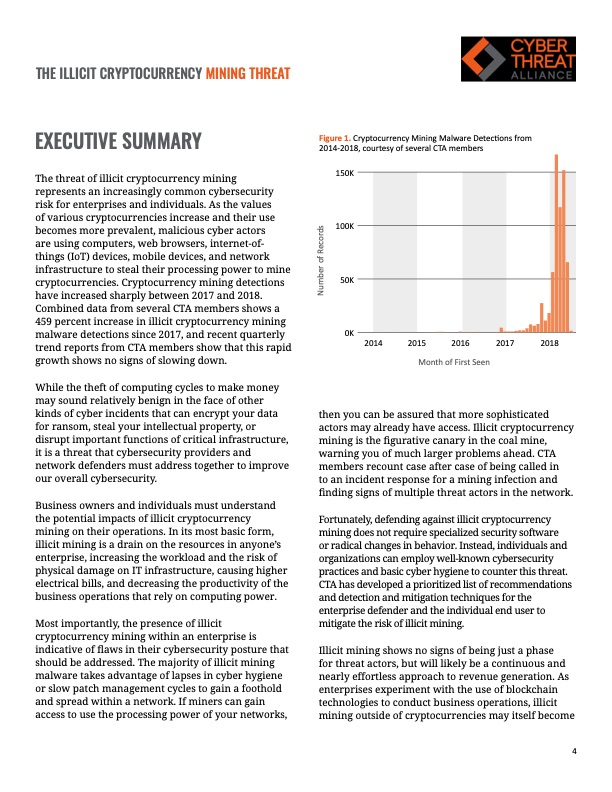
THE ILLICIT CRYPTOCURRENCY MINING THREAT EXECUTIVE SUMMARY The threat of illicit cryptocurrency mining represents an increasingly common cybersecurity risk for enterprises and individuals. As the values of various cryptocurrencies increase and their use becomes more prevalent, malicious cyber actors are using computers, web browsers, internet-of- things (IoT) devices, mobile devices, and network infrastructure to steal their processing power to mine cryptocurrencies. Cryptocurrency mining detections have increased sharply between 2017 and 2018. Combined data from several CTA members shows a 459 percent increase in illicit cryptocurrency mining malware detections since 2017, and recent quarterly trend reports from CTA members show that this rapid growth shows no signs of slowing down. While the theft of computing cycles to make money may sound relatively benign in the face of other kinds of cyber incidents that can encrypt your data for ransom, steal your intellectual property, or disrupt important functions of critical infrastructure, it is a threat that cybersecurity providers and network defenders must address together to improve our overall cybersecurity. Business owners and individuals must understand the potential impacts of illicit cryptocurrency mining on their operations. In its most basic form, illicit mining is a drain on the resources in anyone’s enterprise, increasing the workload and the risk of physical damage on IT infrastructure, causing higher electrical bills, and decreasing the productivity of the business operations that rely on computing power. Most importantly, the presence of illicit cryptocurrency mining within an enterprise is indicative of flaws in their cybersecurity posture that should be addressed. The majority of illicit mining malware takes advantage of lapses in cyber hygiene or slow patch management cycles to gain a foothold and spread within a network. If miners can gain access to use the processing power of your networks, Figure 1. Cryptocurrency Mining Malware Detections from 2014-2018, courtesy of several CTA members 150K 100K 50K 0K 2014 2015 2016 2017 2018 Month of First Seen then you can be assured that more sophisticated actors may already have access. Illicit cryptocurrency mining is the figurative canary in the coal mine, warning you of much larger problems ahead. CTA members recount case after case of being called in to an incident response for a mining infection and finding signs of multiple threat actors in the network. Fortunately, defending against illicit cryptocurrency mining does not require specialized security software or radical changes in behavior. Instead, individuals and organizations can employ well-known cybersecurity practices and basic cyber hygiene to counter this threat. CTA has developed a prioritized list of recommendations and detection and mitigation techniques for the enterprise defender and the individual end user to mitigate the risk of illicit mining. Illicit mining shows no signs of being just a phase for threat actors, but will likely be a continuous and nearly effortless approach to revenue generation. As enterprises experiment with the use of blockchain technologies to conduct business operations, illicit mining outside of cryptocurrencies may itself become 4 Number of RecordsPDF Image | ILLICIT CRYPTOCURRENCY MINING THREAT
PDF Search Title:
ILLICIT CRYPTOCURRENCY MINING THREATOriginal File Name Searched:
CTA-Illicit-CryptoMining-Whitepaper.pdfDIY PDF Search: Google It | Yahoo | Bing
NFT (Non Fungible Token): Buy our tech, design, development or system NFT and become part of our tech NFT network... More Info
IT XR Project Redstone NFT Available for Sale: NFT for high tech turbine design with one part 3D printed counter-rotating energy turbine. Be part of the future with this NFT. Can be bought and sold but only one design NFT exists. Royalties go to the developer (Infinity) to keep enhancing design and applications... More Info
Infinity Turbine IT XR Project Redstone Design: NFT for sale... NFT for high tech turbine design with one part 3D printed counter-rotating energy turbine. Includes all rights to this turbine design, including license for Fluid Handling Block I and II for the turbine assembly and housing. The NFT includes the blueprints (cad/cam), revenue streams, and all future development of the IT XR Project Redstone... More Info
Infinity Turbine ROT Radial Outflow Turbine 24 Design and Worldwide Rights: NFT for sale... NFT for the ROT 24 energy turbine. Be part of the future with this NFT. This design can be bought and sold but only one design NFT exists. You may manufacture the unit, or get the revenues from its sale from Infinity Turbine. Royalties go to the developer (Infinity) to keep enhancing design and applications... More Info
Infinity Supercritical CO2 10 Liter Extractor Design and Worldwide Rights: The Infinity Supercritical 10L CO2 extractor is for botanical oil extraction, which is rich in terpenes and can produce shelf ready full spectrum oil. With over 5 years of development, this industry leader mature extractor machine has been sold since 2015 and is part of many profitable businesses. The process can also be used for electrowinning, e-waste recycling, and lithium battery recycling, gold mining electronic wastes, precious metals. CO2 can also be used in a reverse fuel cell with nafion to make a gas-to-liquids fuel, such as methanol, ethanol and butanol or ethylene. Supercritical CO2 has also been used for treating nafion to make it more effective catalyst. This NFT is for the purchase of worldwide rights which includes the design. More Info
NFT (Non Fungible Token): Buy our tech, design, development or system NFT and become part of our tech NFT network... More Info
Infinity Turbine Products: Special for this month, any plans are $10,000 for complete Cad/Cam blueprints. License is for one build. Try before you buy a production license. May pay by Bitcoin or other Crypto. Products Page... More Info
| CONTACT TEL: 608-238-6001 Email: greg@infinityturbine.com | RSS | AMP |