
PDF Publication Title:
Text from PDF Page: 015
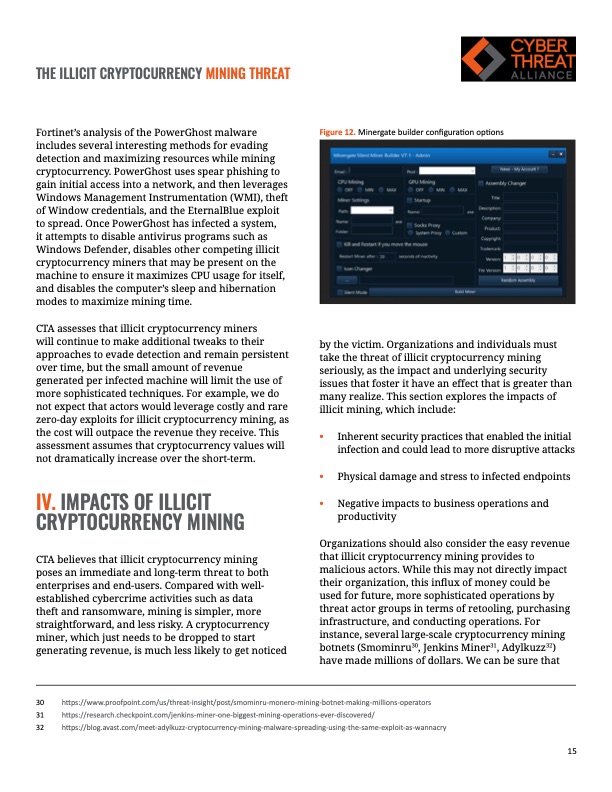
THE ILLICIT CRYPTOCURRENCY MINING THREAT Fortinet’s analysis of the PowerGhost malware includes several interesting methods for evading detection and maximizing resources while mining cryptocurrency. PowerGhost uses spear phishing to gain initial access into a network, and then leverages Windows Management Instrumentation (WMI), theft of Window credentials, and the EternalBlue exploit to spread. Once PowerGhost has infected a system, it attempts to disable antivirus programs such as Windows Defender, disables other competing illicit cryptocurrency miners that may be present on the machine to ensure it maximizes CPU usage for itself, and disables the computer’s sleep and hibernation modes to maximize mining time. CTA assesses that illicit cryptocurrency miners will continue to make additional tweaks to their approaches to evade detection and remain persistent over time, but the small amount of revenue generated per infected machine will limit the use of more sophisticated techniques. For example, we do not expect that actors would leverage costly and rare zero-day exploits for illicit cryptocurrency mining, as the cost will outpace the revenue they receive. This assessment assumes that cryptocurrency values will not dramatically increase over the short-term. IV. IMPACTS OF ILLICIT CRYPTOCURRENCY MINING CTA believes that illicit cryptocurrency mining poses an immediate and long-term threat to both enterprises and end-users. Compared with well- established cybercrime activities such as data theft and ransomware, mining is simpler, more straightforward, and less risky. A cryptocurrency miner, which just needs to be dropped to start generating revenue, is much less likely to get noticed Figure 12. Minergate builder configuration options by the victim. Organizations and individuals must take the threat of illicit cryptocurrency mining seriously, as the impact and underlying security issues that foster it have an effect that is greater than many realize. This section explores the impacts of illicit mining, which include: • Inherent security practices that enabled the initial infection and could lead to more disruptive attacks • Physical damage and stress to infected endpoints • Negative impacts to business operations and productivity Organizations should also consider the easy revenue that illicit cryptocurrency mining provides to malicious actors. While this may not directly impact their organization, this influx of money could be used for future, more sophisticated operations by threat actor groups in terms of retooling, purchasing infrastructure, and conducting operations. For instance, several large-scale cryptocurrency mining botnets (Smominru30, Jenkins Miner31, Adylkuzz32) have made millions of dollars. We can be sure that 30 https://www.proofpoint.com/us/threat-insight/post/smominru-monero-mining-botnet-making-millions-operators 31 https://research.checkpoint.com/jenkins-miner-one-biggest-mining-operations-ever-discovered/ 32 https://blog.avast.com/meet-adylkuzz-cryptocurrency-mining-malware-spreading-using-the-same-exploit-as-wannacry 15PDF Image | ILLICIT CRYPTOCURRENCY MINING THREAT
PDF Search Title:
ILLICIT CRYPTOCURRENCY MINING THREATOriginal File Name Searched:
CTA-Illicit-CryptoMining-Whitepaper.pdfDIY PDF Search: Google It | Yahoo | Bing
NFT (Non Fungible Token): Buy our tech, design, development or system NFT and become part of our tech NFT network... More Info
IT XR Project Redstone NFT Available for Sale: NFT for high tech turbine design with one part 3D printed counter-rotating energy turbine. Be part of the future with this NFT. Can be bought and sold but only one design NFT exists. Royalties go to the developer (Infinity) to keep enhancing design and applications... More Info
Infinity Turbine IT XR Project Redstone Design: NFT for sale... NFT for high tech turbine design with one part 3D printed counter-rotating energy turbine. Includes all rights to this turbine design, including license for Fluid Handling Block I and II for the turbine assembly and housing. The NFT includes the blueprints (cad/cam), revenue streams, and all future development of the IT XR Project Redstone... More Info
Infinity Turbine ROT Radial Outflow Turbine 24 Design and Worldwide Rights: NFT for sale... NFT for the ROT 24 energy turbine. Be part of the future with this NFT. This design can be bought and sold but only one design NFT exists. You may manufacture the unit, or get the revenues from its sale from Infinity Turbine. Royalties go to the developer (Infinity) to keep enhancing design and applications... More Info
Infinity Supercritical CO2 10 Liter Extractor Design and Worldwide Rights: The Infinity Supercritical 10L CO2 extractor is for botanical oil extraction, which is rich in terpenes and can produce shelf ready full spectrum oil. With over 5 years of development, this industry leader mature extractor machine has been sold since 2015 and is part of many profitable businesses. The process can also be used for electrowinning, e-waste recycling, and lithium battery recycling, gold mining electronic wastes, precious metals. CO2 can also be used in a reverse fuel cell with nafion to make a gas-to-liquids fuel, such as methanol, ethanol and butanol or ethylene. Supercritical CO2 has also been used for treating nafion to make it more effective catalyst. This NFT is for the purchase of worldwide rights which includes the design. More Info
NFT (Non Fungible Token): Buy our tech, design, development or system NFT and become part of our tech NFT network... More Info
Infinity Turbine Products: Special for this month, any plans are $10,000 for complete Cad/Cam blueprints. License is for one build. Try before you buy a production license. May pay by Bitcoin or other Crypto. Products Page... More Info
| CONTACT TEL: 608-238-6001 Email: greg@infinityturbine.com | RSS | AMP |