
PDF Publication Title:
Text from PDF Page: 013
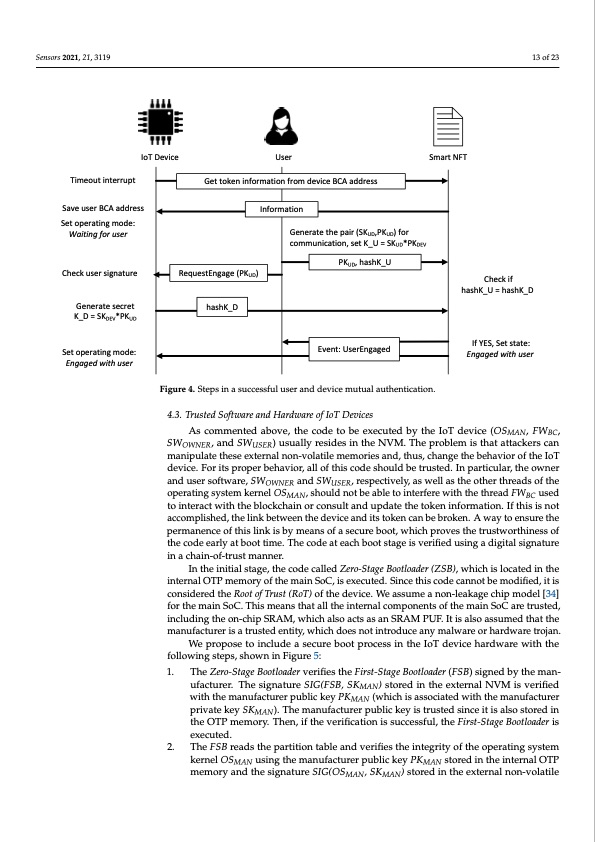
Sensors 2021, 21, 3119 Sensors 2021, 21, x FOR PEER REVIEW 13 of 23 14 of 23 IoT Device User Smart NFT Timeout interrupt Save user BCA address Set operating mode: Waiting for user Check user signature Generate secret K_D = SKDEV*PKUD FFiiggurree44..SSteteppssininaassuuccceesssffuulluusseerraannddeevviicceemuttuaallaauttheenttiiccattiion.. 4.3. Trusted Software and Hardware of IoT Devices 4.3. Trusted Software and Hardware of IoT Devices As commented above, the code to be executed by the IoT device (OSMAN, FWBC, As commented above, the code to be executed by the IoT device (OSMAN, FWBC, SWOWNER, and SWUSER) usually resides in the NVM. The problem is that attackers can ma- SWOWNER, and SWUSER) usually resides in the NVM. The problem is that attackers can nipulate these external non-volatile memories and, thus, change the behavior of the IoT manipulate these external non-volatile memories and, thus, change the behavior of the IoT device. For its proper behavior, all of this code should be trusted. In particular, the owner device. For its proper behavior, all of this code should be trusted. In particular, the owner and user software, SWOWNER and SWUSER, respectively, as well as the other threads of the and user software, SWOWNER and SWUSER, respectively, as well as the other threads of the ooppeerraattiingssysttemkernelOSMAN, s,hshoouuldldnnoottbbeeaabbleletotoinintteerrffeerrewiitthtthethreadFWBC usseed MAN BC totoinintteerraaccttwitithhtthheebblloocckkcchhaaininorrcconssullttaandupdaatteettheettokeniinfforrmattiion..IIfftthiissiissnott aacccoomplliisshed,,thelinkbetweenttheddeevviciceeaanndditiststotkoeknencacnanbebberbokroekne.nA.Awawyatyoetonseunrseutrhee tpherpmearmneancenocfetohfisthlisnkliniskbisybmyemanesanosfoafsaecsuecruerbeoboot,owt,hwichhicphrporvoevsetshtehterutrsutwstowrothrtihneinsessosf otfhtehceocdoedeaeralyrlaytabtoboototitmtiem.eT.hTehceocdoedaetaetaecahcbhobootostasgtaegiesvisevriefireifdieudsiunsginagdaigdiitgalitsailgsniagtnuar-e tuinreaicnhaicnh-oaifn-t-roufs-trmusatnmnearn.ner. IInnththeeininititiaiallsstataggee,,tthheeccooddeeccaalleleddZeerroo--SSttaaggeeBooottllooaaddeerr((ZSB)),,whiicchiisslloccattediintthee inintteerrnaallOTPmemory of the main SoC,,iisexeccutteed..Siincceetthhisisccooddeeccaannnoot tbbeemmododifiiefide,di,tiits iscocnosnisdiedrerdedthtehReoRoototfoTfruTsrtu(sRto(RT)oTo)ftohfethdevdiecve.icWe.eWasesuasmsuemaenoann-loena-klaeagkeacgheipchmipodmelo[d3e4l] for the main SoC. This means that all the internal components of the main SoC are trusted, [34] for the main SoC. This means that all the internal components of the main SoC are including the on-chip SRAM, which also acts as an SRAM PUF. It is also assumed that the trusted, including the on-chip SRAM, which also acts as an SRAM PUF. It is also assumed manufacturer is a trusted entity, which does not introduce any malware or hardware trojan. that the manufacturer is a trusted entity, which does not introduce any malware or hard- 1. 2. 2. ufacturer. The signature SIG(FSB, SK ) stored in the external NVM is verified The Zero-Stage Bootloader verifies the FirMstA-SNtage Bootloader (FSB) signed by the manu- with the manufacturer public key PK (which is associated with the manufacturer Get token information from device BCA address hashK_D Information Generate the pair (SKUD,PKUD) for communication, set K_U = SKUD*PKDEV PKUD, hashK_U RequestEngage (PKUD) We propose to include a secure boot process in the IoT device hardware with the ware trojan. following steps, shown in Figure 5: We propose to include a secure boot process in the IoT device hardware with the f1o.llowTinhge sZterpos-,SsthagoewBnoointloFaidgeurrvee5r:ifies the First-Stage Bootloader (FSB) signed by the man- Check if hashK_U = hashK_D Set operating mode: Engaged with user Event: UserEngaged facturer. The signature SIG(FSB, SKMAN) stored in the external NVM is verified with MAN private key SK the manufacturer public key PKMAN (which is associated with the manufacturer pri- ). The manufacturer public key is trusted since it is also stored in the OTP memory. Then, if the verification is successful, the First-Stage Bootloader is MAN vate key SKMAN). The manufacturer public key is trusted since it is also stored in the executed. OTP memory. Then, if the verification is successful, the First-Stage Bootloader is exe- The FSB reads the partition table and verifies the integrity of the operating system cuted. kernel OSMAN using the manufacturer public key PKMAN stored in the internal OTP The FSB reads the partition table and verifies the integrity of the operating system memory and the signature SIG(OSMAN, SKMAN) stored in the external non-volatile kernel OSMAN using the manufacturer public key PKMAN stored in the internal OTP If YES, Set state: Engaged with userPDF Image | Binding IOT to Smart Non-Fungible Tokens Using PUF
PDF Search Title:
Binding IOT to Smart Non-Fungible Tokens Using PUFOriginal File Name Searched:
sensors-21-03119.pdfDIY PDF Search: Google It | Yahoo | Bing
NFT (Non Fungible Token): Buy our tech, design, development or system NFT and become part of our tech NFT network... More Info
IT XR Project Redstone NFT Available for Sale: NFT for high tech turbine design with one part 3D printed counter-rotating energy turbine. Be part of the future with this NFT. Can be bought and sold but only one design NFT exists. Royalties go to the developer (Infinity) to keep enhancing design and applications... More Info
Infinity Turbine IT XR Project Redstone Design: NFT for sale... NFT for high tech turbine design with one part 3D printed counter-rotating energy turbine. Includes all rights to this turbine design, including license for Fluid Handling Block I and II for the turbine assembly and housing. The NFT includes the blueprints (cad/cam), revenue streams, and all future development of the IT XR Project Redstone... More Info
Infinity Turbine ROT Radial Outflow Turbine 24 Design and Worldwide Rights: NFT for sale... NFT for the ROT 24 energy turbine. Be part of the future with this NFT. This design can be bought and sold but only one design NFT exists. You may manufacture the unit, or get the revenues from its sale from Infinity Turbine. Royalties go to the developer (Infinity) to keep enhancing design and applications... More Info
Infinity Supercritical CO2 10 Liter Extractor Design and Worldwide Rights: The Infinity Supercritical 10L CO2 extractor is for botanical oil extraction, which is rich in terpenes and can produce shelf ready full spectrum oil. With over 5 years of development, this industry leader mature extractor machine has been sold since 2015 and is part of many profitable businesses. The process can also be used for electrowinning, e-waste recycling, and lithium battery recycling, gold mining electronic wastes, precious metals. CO2 can also be used in a reverse fuel cell with nafion to make a gas-to-liquids fuel, such as methanol, ethanol and butanol or ethylene. Supercritical CO2 has also been used for treating nafion to make it more effective catalyst. This NFT is for the purchase of worldwide rights which includes the design. More Info
NFT (Non Fungible Token): Buy our tech, design, development or system NFT and become part of our tech NFT network... More Info
Infinity Turbine Products: Special for this month, any plans are $10,000 for complete Cad/Cam blueprints. License is for one build. Try before you buy a production license. May pay by Bitcoin or other Crypto. Products Page... More Info
| CONTACT TEL: 608-238-6001 Email: greg@infinityturbine.com | RSS | AMP |