
PDF Publication Title:
Text from PDF Page: 014
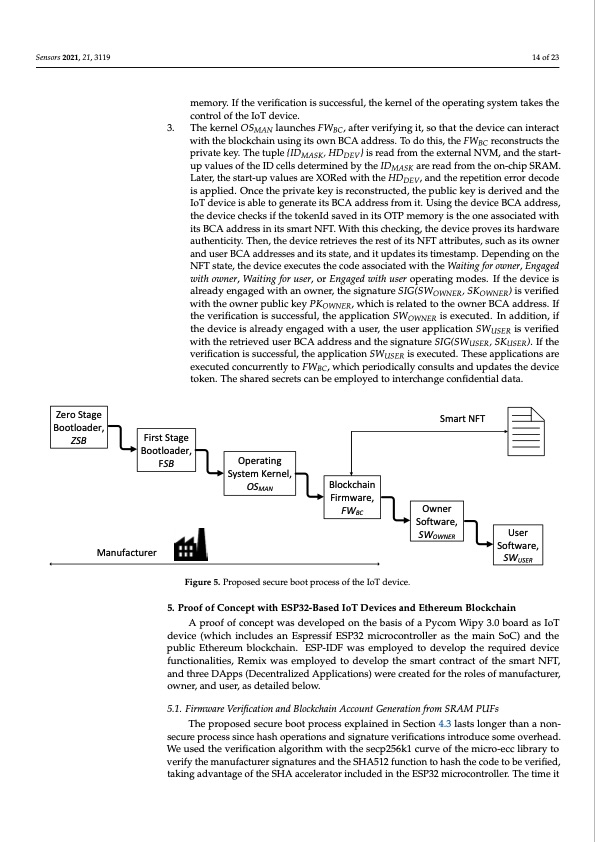
Sensors 2021, 21, x FOR PEER REVIEW Sensors 2021, 21, 3119 15 of 23 14 of 23 memory and the signature SIG(OSMAN, SKMAN) stored in the external non-volatile meemooryry..IfIfththeevveerrifiificcaattioionnisisssuccceesssffull,,ttheekeerrnelloffttheoperrattiingsysttemttakestthe ccoonntrtorollooffththeeIoIoTTddeevvicicee.. The kernel OS launches FW , after verifying it, so that the device can interact The kernel OSMMANANlaunches FWBCB,Cafter verifying it, so that the device can interact 3. 3. with the blockchain using its own BCA address. To do this, the FW reconstructs the BC with the blockchain using its own BCA address. To do this, the FWBC reconstructs the private key. The tuple {ID , HD } is read from the external NVM, and the start- MASK DEV private key. The tuple {IDMASK, HDDEV} is read from the external NVM, and the start- up values of the ID cells determined by the IDMASK are read from the on-chip SRAM. up values of the ID cells determined by the IDMASK are read from the on-chip SRAM. Later, the start-up values are XORed with the HDDEV, and the repetition error decode Later, the start-up values are XORed with the HDDEV, and the repetition error decode is applied. Once the private key is reconstructed, the public key is derived and the is applied. Once the private key is reconstructed, the public key is derived and the IoT device is able to generate its BCA address from it. Using the device BCA address, IoT device is able to generate its BCA address from it. Using the device BCA address, the device checks if the tokenId saved in its OTP memory is the one associated with the device checks if the tokenId saved in its OTP memory is the one associated with its BCA address in its smart NFT. With this checking, the device proves its hardware its BCA address in its smart NFT. With this checking, the device proves its hardware authenticity. Then, the device retrieves the rest of its NFT attributes, such as its owner authenticity. Then, the device retrieves the rest of its NFT attributes, such as its owner and user BCA addresses and its state, and it updates its timestamp. Depending on the and user BCA addresses and its state, and it updates its timestamp. Depending on NFT state, the device executes the code associated with the Waiting for owner, Engaged the NFT state, the device executes the code associated with the Waiting for owner, En- with owner, Waiting for user, or Engaged with user operating modes. If the device is gaged with owner, Waiting for user, or Engaged with user operating modes. If the device already engaged with an owner, the signature SIG(SWOWNER, SKOWNER) is verified is already engaged with an owner, the signature SIG(SWOWNER, SKOWNER) is verified with the owner public key PKOWNER, which is related to the owner BCA address. If with the owner public key PKOWNER, which is related to the owner BCA address. If the the verification is successful, the application SWOWNER is executed. In addition, if verification is successful, the application SWOWNER is executed. In addition, if the de- the device is already engaged with a user, the user application SWUSER is verified vice is already engaged with a user, the user application SWUSER is verified with the with the retrieved user BCA address and the signature SIG(SWUSER, SKUSER). If the retrieved user BCA address and the signature SIG(SWUSER, SKUSER). If the verification verification is successful, the application SWUSER is executed. These applications are is successful, the application SWUSER is executed. These applications are executed con- executed concurrently to FWBC, which periodically consults and updates the device currently to FWBC, which periodically consults and updates the device token. The token. The shared secrets can be employed to interchange confidential data. shared secrets can be employed to interchange confidential data. Zero Stage Bootloader, ZSB Manufacturer Figure 5. Proposed secure boot process of the IoT device. Figure 5. Proposed secure boot process of the IoT device. 5. Proof of Concept with ESP32-Based IoT Devices and Ethereum Blockchain 5. Proof of Concept with ESP32-Based IoT Devices and Ethereum Blockchain A proof of concept was developed on the basis of a Pycom Wipy 3.0 board as IoT A proof of concept was developed on the basis of a Pycom Wipy 3.0 board as IoT device (which includes an Espressif ESP32 microcontroller as the main SoC) and the device (which includes an Espressif ESP32 microcontroller as the main SoC) and the pub- public Ethereum blockchain. ESP-IDF was employed to develop the required device lic Ethereum blockchain. ESP-IDF was employed to develop the required device function- functionalities, Remix was employed to develop the smart contract of the smart NFT, alities, Remix was employed to develop the smart contract of the smart NFT, and three and three DApps (Decentralized Applications) were created for the roles of manufacturer, DApps (Decentralized Applications) were created for the roles of manufacturer, owner, owner, and user, as detailed below. and user, as detailed below. 5.1. Firmware Verification and Blockchain Account Generation from SRAM PUFs 5.1. Firmware Verification and Blockchain Account Generation from SRAM PUFs The proposed secure boot process explained in Section 4.3 lasts longer than a non- The proposed secure boot process explained in Section 4.3 lasts longer than a non- secure process since hash operations and signature verifications introduce some overhead. secure process since hash operations and signature verifications introduce some over- We used the verification algorithm with the secp256k1 curve of the micro-ecc library to head. We used the verification algorithm with the secp256k1 curve of the micro-ecc library verify the manufacturer signatures and the SHA512 function to hash the code to be verified, to verify the manufacturer signatures and the SHA512 function to hash the code to be taking advantage of the SHA accelerator included in the ESP32 microcontroller. The time it Smart NFT First Stage Bootloader, FSB Operating System Kernel, OSMAN Blockchain Firmware, FWBC Owner Software, SWOWNER User Software, SWUSERPDF Image | Binding IOT to Smart Non-Fungible Tokens Using PUF
PDF Search Title:
Binding IOT to Smart Non-Fungible Tokens Using PUFOriginal File Name Searched:
sensors-21-03119.pdfDIY PDF Search: Google It | Yahoo | Bing
NFT (Non Fungible Token): Buy our tech, design, development or system NFT and become part of our tech NFT network... More Info
IT XR Project Redstone NFT Available for Sale: NFT for high tech turbine design with one part 3D printed counter-rotating energy turbine. Be part of the future with this NFT. Can be bought and sold but only one design NFT exists. Royalties go to the developer (Infinity) to keep enhancing design and applications... More Info
Infinity Turbine IT XR Project Redstone Design: NFT for sale... NFT for high tech turbine design with one part 3D printed counter-rotating energy turbine. Includes all rights to this turbine design, including license for Fluid Handling Block I and II for the turbine assembly and housing. The NFT includes the blueprints (cad/cam), revenue streams, and all future development of the IT XR Project Redstone... More Info
Infinity Turbine ROT Radial Outflow Turbine 24 Design and Worldwide Rights: NFT for sale... NFT for the ROT 24 energy turbine. Be part of the future with this NFT. This design can be bought and sold but only one design NFT exists. You may manufacture the unit, or get the revenues from its sale from Infinity Turbine. Royalties go to the developer (Infinity) to keep enhancing design and applications... More Info
Infinity Supercritical CO2 10 Liter Extractor Design and Worldwide Rights: The Infinity Supercritical 10L CO2 extractor is for botanical oil extraction, which is rich in terpenes and can produce shelf ready full spectrum oil. With over 5 years of development, this industry leader mature extractor machine has been sold since 2015 and is part of many profitable businesses. The process can also be used for electrowinning, e-waste recycling, and lithium battery recycling, gold mining electronic wastes, precious metals. CO2 can also be used in a reverse fuel cell with nafion to make a gas-to-liquids fuel, such as methanol, ethanol and butanol or ethylene. Supercritical CO2 has also been used for treating nafion to make it more effective catalyst. This NFT is for the purchase of worldwide rights which includes the design. More Info
NFT (Non Fungible Token): Buy our tech, design, development or system NFT and become part of our tech NFT network... More Info
Infinity Turbine Products: Special for this month, any plans are $10,000 for complete Cad/Cam blueprints. License is for one build. Try before you buy a production license. May pay by Bitcoin or other Crypto. Products Page... More Info
| CONTACT TEL: 608-238-6001 Email: greg@infinityturbine.com | RSS | AMP |