
PDF Publication Title:
Text from PDF Page: 003
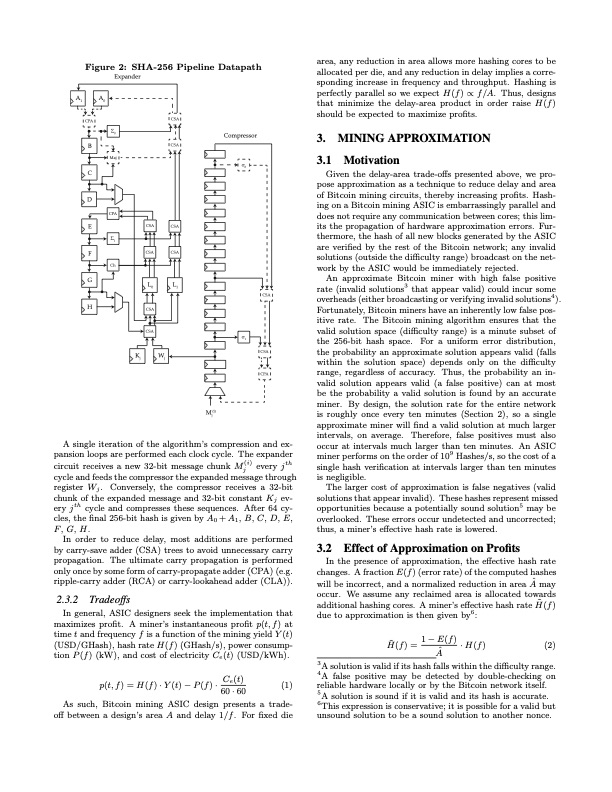
A1 A0 B Maj C D CPA E Σ 1 F Ch G H Figure 2: SHA-256 Pipeline Datapath area, any reduction in area allows more hashing cores to be allocated per die, and any reduction in delay implies a corre- sponding increase in frequency and throughput. Hashing is perfectly parallel so we expect H(f) ∝ f/A. Thus, designs that minimize the delay-area product in order raise H(f) should be expected to maximize profits. 3. MINING APPROXIMATION 3.1 Motivation Given the delay-area trade-offs presented above, we pro- pose approximation as a technique to reduce delay and area of Bitcoin mining circuits, thereby increasing profits. Hash- ing on a Bitcoin mining ASIC is embarrassingly parallel and does not require any communication between cores; this lim- its the propagation of hardware approximation errors. Fur- thermore, the hash of all new blocks generated by the ASIC are verified by the rest of the Bitcoin network; any invalid solutions (outside the difficulty range) broadcast on the net- work by the ASIC would be immediately rejected. An approximate Bitcoin miner with high false positive rate (invalid solutions3 that appear valid) could incur some overheads (either broadcasting or verifying invalid solutions4). Fortunately, Bitcoin miners have an inherently low false pos- itive rate. The Bitcoin mining algorithm ensures that the valid solution space (difficulty range) is a minute subset of the 256-bit hash space. For a uniform error distribution, the probability an approximate solution appears valid (falls within the solution space) depends only on the difficulty range, regardless of accuracy. Thus, the probability an in- valid solution appears valid (a false positive) can at most be the probability a valid solution is found by an accurate miner. By design, the solution rate for the entire network is roughly once every ten minutes (Section 2), so a single approximate miner will find a valid solution at much larger intervals, on average. Therefore, false positives must also occur at intervals much larger than ten minutes. An ASIC miner performs on the order of 109 Hashes/s, so the cost of a single hash verification at intervals larger than ten minutes is negligible. The larger cost of approximation is false negatives (valid solutions that appear invalid). These hashes represent missed opportunities because a potentially sound solution5 may be overlooked. These errors occur undetected and uncorrected; thus, a miner’s effective hash rate is lowered. 3.2 Effect of Approximation on Profits In the presence of approximation, the effective hash rate changes. A fraction E(f) (error rate) of the computed hashes will be incorrect, and a normalized reduction in area Aˆ may occur. We assume any reclaimed area is allocated towards additional hashing cores. A miner’s effective hash rate H ̃ (f ) due to approximation is then given by6: CPA CSA CSA CSA CSA L1 Σ 0 Compressor Expander σ 0 Kj Wj CSA CSA L0 CSA CSA CSA σ CSA CPA 1 A single iteration of the algorithm’s compression and ex- pansion loops are performed each clock cycle. The expander circuit receives a new 32-bit message chunk M(i) every jth j cycle and feeds the compressor the expanded message through register Wj. Conversely, the compressor receives a 32-bit chunk of the expanded message and 32-bit constant Kj ev- ery jth cycle and compresses these sequences. After 64 cy- cles, the final 256-bit hash is given by A0 +A1, B, C, D, E, F, G, H. In order to reduce delay, most additions are performed by carry-save adder (CSA) trees to avoid unnecessary carry propagation. The ultimate carry propagation is performed only once by some form of carry-propagate adder (CPA) (e.g. ripple-carry adder (RCA) or carry-lookahead adder (CLA)). 2.3.2 Tradeoffs In general, ASIC designers seek the implementation that maximizes profit. A miner’s instantaneous profit p(t,f) at time t and frequency f is a function of the mining yield Y (t) (USD/GHash), hash rate H(f) (GHash/s), power consump- tion P(f) (kW), and cost of electricity Ce(t) (USD/kWh). 1−E(f) H ̃ ( f ) = Aˆ · H ( f ) ( 2 ) M (i) j p(t,f) = H(f)·Y(t)−P(f)· Ce (t) 60·60 (1) 3A solution is valid if its hash falls within the difficulty range. 4A false positive may be detected by double-checking on reliable hardware locally or by the Bitcoin network itself. 5A solution is sound if it is valid and its hash is accurate. 6This expression is conservative; it is possible for a valid but unsound solution to be a sound solution to another nonce. As such, Bitcoin mining ASIC design presents a trade- off between a design’s area A and delay 1/f. For fixed diePDF Image | Approximate Bitcoin Mining
PDF Search Title:
Approximate Bitcoin MiningOriginal File Name Searched:
dac_16_cam.pdfDIY PDF Search: Google It | Yahoo | Bing
NFT (Non Fungible Token): Buy our tech, design, development or system NFT and become part of our tech NFT network... More Info
IT XR Project Redstone NFT Available for Sale: NFT for high tech turbine design with one part 3D printed counter-rotating energy turbine. Be part of the future with this NFT. Can be bought and sold but only one design NFT exists. Royalties go to the developer (Infinity) to keep enhancing design and applications... More Info
Infinity Turbine IT XR Project Redstone Design: NFT for sale... NFT for high tech turbine design with one part 3D printed counter-rotating energy turbine. Includes all rights to this turbine design, including license for Fluid Handling Block I and II for the turbine assembly and housing. The NFT includes the blueprints (cad/cam), revenue streams, and all future development of the IT XR Project Redstone... More Info
Infinity Turbine ROT Radial Outflow Turbine 24 Design and Worldwide Rights: NFT for sale... NFT for the ROT 24 energy turbine. Be part of the future with this NFT. This design can be bought and sold but only one design NFT exists. You may manufacture the unit, or get the revenues from its sale from Infinity Turbine. Royalties go to the developer (Infinity) to keep enhancing design and applications... More Info
Infinity Supercritical CO2 10 Liter Extractor Design and Worldwide Rights: The Infinity Supercritical 10L CO2 extractor is for botanical oil extraction, which is rich in terpenes and can produce shelf ready full spectrum oil. With over 5 years of development, this industry leader mature extractor machine has been sold since 2015 and is part of many profitable businesses. The process can also be used for electrowinning, e-waste recycling, and lithium battery recycling, gold mining electronic wastes, precious metals. CO2 can also be used in a reverse fuel cell with nafion to make a gas-to-liquids fuel, such as methanol, ethanol and butanol or ethylene. Supercritical CO2 has also been used for treating nafion to make it more effective catalyst. This NFT is for the purchase of worldwide rights which includes the design. More Info
NFT (Non Fungible Token): Buy our tech, design, development or system NFT and become part of our tech NFT network... More Info
Infinity Turbine Products: Special for this month, any plans are $10,000 for complete Cad/Cam blueprints. License is for one build. Try before you buy a production license. May pay by Bitcoin or other Crypto. Products Page... More Info
| CONTACT TEL: 608-238-6001 Email: greg@infinityturbine.com | RSS | AMP |