
PDF Publication Title:
Text from PDF Page: 003
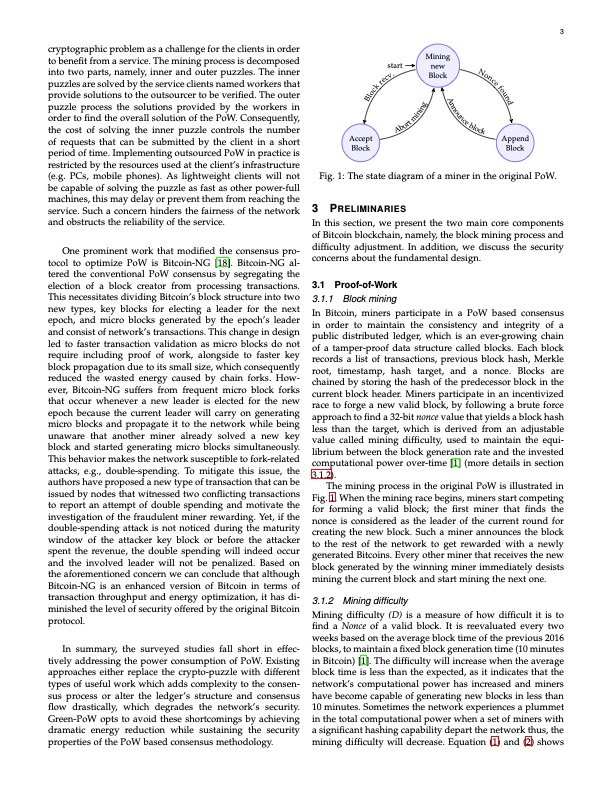
cryptographic problem as a challenge for the clients in order to benefit from a service. The mining process is decomposed into two parts, namely, inner and outer puzzles. The inner puzzles are solved by the service clients named workers that provide solutions to the outsourcer to be verified. The outer puzzle process the solutions provided by the workers in order to find the overall solution of the PoW. Consequently, the cost of solving the inner puzzle controls the number of requests that can be submitted by the client in a short period of time. Implementing outsourced PoW in practice is restricted by the resources used at the client’s infrastructure (e.g. PCs, mobile phones). As lightweight clients will not be capable of solving the puzzle as fast as other power-full machines, this may delay or prevent them from reaching the service. Such a concern hinders the fairness of the network and obstructs the reliability of the service. One prominent work that modified the consensus pro- tocol to optimize PoW is Bitcoin-NG [18]. Bitcoin-NG al- tered the conventional PoW consensus by segregating the election of a block creator from processing transactions. This necessitates dividing Bitcoin’s block structure into two new types, key blocks for electing a leader for the next epoch, and micro blocks generated by the epoch’s leader and consist of network’s transactions. This change in design led to faster transaction validation as micro blocks do not require including proof of work, alongside to faster key block propagation due to its small size, which consequently reduced the wasted energy caused by chain forks. How- ever, Bitcoin-NG suffers from frequent micro block forks that occur whenever a new leader is elected for the new epoch because the current leader will carry on generating micro blocks and propagate it to the network while being unaware that another miner already solved a new key block and started generating micro blocks simultaneously. This behavior makes the network susceptible to fork-related attacks, e.g., double-spending. To mitigate this issue, the authors have proposed a new type of transaction that can be issued by nodes that witnessed two conflicting transactions to report an attempt of double spending and motivate the investigation of the fraudulent miner rewarding. Yet, if the double-spending attack is not noticed during the maturity window of the attacker key block or before the attacker spent the revenue, the double spending will indeed occur and the involved leader will not be penalized. Based on the aforementioned concern we can conclude that although Bitcoin-NG is an enhanced version of Bitcoin in terms of transaction throughput and energy optimization, it has di- minished the level of security offered by the original Bitcoin protocol. In summary, the surveyed studies fall short in effec- tively addressing the power consumption of PoW. Existing approaches either replace the crypto-puzzle with different types of useful work which adds complexity to the consen- sus process or alter the ledger’s structure and consensus flow drastically, which degrades the network’s security. Green-PoW opts to avoid these shortcomings by achieving dramatic energy reduction while sustaining the security properties of the PoW based consensus methodology. start Mining new Block 3 Accept Block Append Block Fig. 1: The state diagram of a miner in the original PoW. 3 PRELIMINARIES In this section, we present the two main core components of Bitcoin blockchain, namely, the block mining process and difficulty adjustment. In addition, we discuss the security concerns about the fundamental design. 3.1 Proof-of-Work 3.1.1 Block mining In Bitcoin, miners participate in a PoW based consensus in order to maintain the consistency and integrity of a public distributed ledger, which is an ever-growing chain of a tamper-proof data structure called blocks. Each block records a list of transactions, previous block hash, Merkle root, timestamp, hash target, and a nonce. Blocks are chained by storing the hash of the predecessor block in the current block header. Miners participate in an incentivized race to forge a new valid block, by following a brute force approach to find a 32-bit nonce value that yields a block hash less than the target, which is derived from an adjustable value called mining difficulty, used to maintain the equi- librium between the block generation rate and the invested computational power over-time [1] (more details in section 3.1.2). The mining process in the original PoW is illustrated in Fig. 1. When the mining race begins, miners start competing for forming a valid block; the first miner that finds the nonce is considered as the leader of the current round for creating the new block. Such a miner announces the block to the rest of the network to get rewarded with a newly generated Bitcoins. Every other miner that receives the new block generated by the winning miner immediately desists mining the current block and start mining the next one. 3.1.2 Mining difficulty Mining difficulty (D) is a measure of how difficult it is to find a Nonce of a valid block. It is reevaluated every two weeks based on the average block time of the previous 2016 blocks, to maintain a fixed block generation time (10 minutes in Bitcoin) [1]. The difficulty will increase when the average block time is less than the expected, as it indicates that the network’s computational power has increased and miners have become capable of generating new blocks in less than 10 minutes. Sometimes the network experiences a plummet in the total computational power when a set of miners with a significant hashing capability depart the network thus, the mining difficulty will decrease. Equation (1) and (2) shows . v N c o n r t e c e k c f o o u l n B A d g n n n i n o i u m n r c o e b A b l o c kPDF Image | Efficient Blockchain Proof-of-Work Consensus Algorithm
PDF Search Title:
Efficient Blockchain Proof-of-Work Consensus AlgorithmOriginal File Name Searched:
2007-04086.pdfDIY PDF Search: Google It | Yahoo | Bing
NFT (Non Fungible Token): Buy our tech, design, development or system NFT and become part of our tech NFT network... More Info
IT XR Project Redstone NFT Available for Sale: NFT for high tech turbine design with one part 3D printed counter-rotating energy turbine. Be part of the future with this NFT. Can be bought and sold but only one design NFT exists. Royalties go to the developer (Infinity) to keep enhancing design and applications... More Info
Infinity Turbine IT XR Project Redstone Design: NFT for sale... NFT for high tech turbine design with one part 3D printed counter-rotating energy turbine. Includes all rights to this turbine design, including license for Fluid Handling Block I and II for the turbine assembly and housing. The NFT includes the blueprints (cad/cam), revenue streams, and all future development of the IT XR Project Redstone... More Info
Infinity Turbine ROT Radial Outflow Turbine 24 Design and Worldwide Rights: NFT for sale... NFT for the ROT 24 energy turbine. Be part of the future with this NFT. This design can be bought and sold but only one design NFT exists. You may manufacture the unit, or get the revenues from its sale from Infinity Turbine. Royalties go to the developer (Infinity) to keep enhancing design and applications... More Info
Infinity Supercritical CO2 10 Liter Extractor Design and Worldwide Rights: The Infinity Supercritical 10L CO2 extractor is for botanical oil extraction, which is rich in terpenes and can produce shelf ready full spectrum oil. With over 5 years of development, this industry leader mature extractor machine has been sold since 2015 and is part of many profitable businesses. The process can also be used for electrowinning, e-waste recycling, and lithium battery recycling, gold mining electronic wastes, precious metals. CO2 can also be used in a reverse fuel cell with nafion to make a gas-to-liquids fuel, such as methanol, ethanol and butanol or ethylene. Supercritical CO2 has also been used for treating nafion to make it more effective catalyst. This NFT is for the purchase of worldwide rights which includes the design. More Info
NFT (Non Fungible Token): Buy our tech, design, development or system NFT and become part of our tech NFT network... More Info
Infinity Turbine Products: Special for this month, any plans are $10,000 for complete Cad/Cam blueprints. License is for one build. Try before you buy a production license. May pay by Bitcoin or other Crypto. Products Page... More Info
| CONTACT TEL: 608-238-6001 Email: greg@infinityturbine.com | RSS | AMP |