
PDF Publication Title:
Text from PDF Page: 022
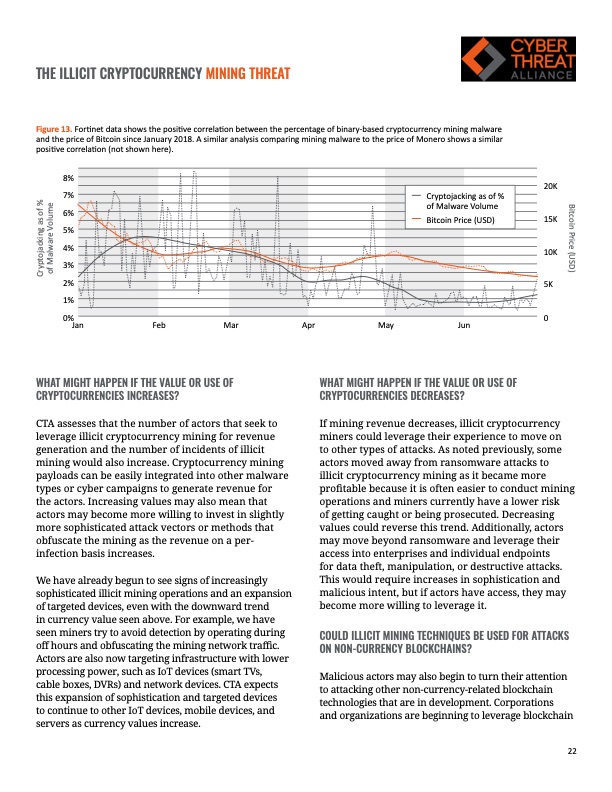
THE ILLICIT CRYPTOCURRENCY MINING THREAT Figure 13. Fortinet data shows the positive correlation between the percentage of binary-based cryptocurrency mining malware and the price of Bitcoin since January 2018. A similar analysis comparing mining malware to the price of Monero shows a similar positive correlation (not shown here). 8% 7% 6% 5% 4% 3% 2% 1% 0% Jan Feb Mar Apr May Jun 20K 15K 10K 5K 0 Cryptojacking as of % of Malware Volume Bitcoin Price (USD) WHAT MIGHT HAPPEN IF THE VALUE OR USE OF CRYPTOCURRENCIES INCREASES? CTA assesses that the number of actors that seek to leverage illicit cryptocurrency mining for revenue generation and the number of incidents of illicit mining would also increase. Cryptocurrency mining payloads can be easily integrated into other malware types or cyber campaigns to generate revenue for the actors. Increasing values may also mean that actors may become more willing to invest in slightly more sophisticated attack vectors or methods that obfuscate the mining as the revenue on a per- infection basis increases. We have already begun to see signs of increasingly sophisticated illicit mining operations and an expansion of targeted devices, even with the downward trend in currency value seen above. For example, we have seen miners try to avoid detection by operating during off hours and obfuscating the mining network traffic. Actors are also now targeting infrastructure with lower processing power, such as IoT devices (smart TVs, cable boxes, DVRs) and network devices. CTA expects this expansion of sophistication and targeted devices to continue to other IoT devices, mobile devices, and servers as currency values increase. WHAT MIGHT HAPPEN IF THE VALUE OR USE OF CRYPTOCURRENCIES DECREASES? If mining revenue decreases, illicit cryptocurrency miners could leverage their experience to move on to other types of attacks. As noted previously, some actors moved away from ransomware attacks to illicit cryptocurrency mining as it became more profitable because it is often easier to conduct mining operations and miners currently have a lower risk of getting caught or being prosecuted. Decreasing values could reverse this trend. Additionally, actors may move beyond ransomware and leverage their access into enterprises and individual endpoints for data theft, manipulation, or destructive attacks. This would require increases in sophistication and malicious intent, but if actors have access, they may become more willing to leverage it. COULD ILLICIT MINING TECHNIQUES BE USED FOR ATTACKS ON NON-CURRENCY BLOCKCHAINS? Malicious actors may also begin to turn their attention to attacking other non-currency-related blockchain technologies that are in development. Corporations and organizations are beginning to leverage blockchain 22 Bitcoin Price (USD) Cryptojacking as of % of Malware VolumePDF Image | ILLICIT CRYPTOCURRENCY MINING THREAT
PDF Search Title:
ILLICIT CRYPTOCURRENCY MINING THREATOriginal File Name Searched:
CTA-Illicit-CryptoMining-Whitepaper.pdfDIY PDF Search: Google It | Yahoo | Bing
NFT (Non Fungible Token): Buy our tech, design, development or system NFT and become part of our tech NFT network... More Info
IT XR Project Redstone NFT Available for Sale: NFT for high tech turbine design with one part 3D printed counter-rotating energy turbine. Be part of the future with this NFT. Can be bought and sold but only one design NFT exists. Royalties go to the developer (Infinity) to keep enhancing design and applications... More Info
Infinity Turbine IT XR Project Redstone Design: NFT for sale... NFT for high tech turbine design with one part 3D printed counter-rotating energy turbine. Includes all rights to this turbine design, including license for Fluid Handling Block I and II for the turbine assembly and housing. The NFT includes the blueprints (cad/cam), revenue streams, and all future development of the IT XR Project Redstone... More Info
Infinity Turbine ROT Radial Outflow Turbine 24 Design and Worldwide Rights: NFT for sale... NFT for the ROT 24 energy turbine. Be part of the future with this NFT. This design can be bought and sold but only one design NFT exists. You may manufacture the unit, or get the revenues from its sale from Infinity Turbine. Royalties go to the developer (Infinity) to keep enhancing design and applications... More Info
Infinity Supercritical CO2 10 Liter Extractor Design and Worldwide Rights: The Infinity Supercritical 10L CO2 extractor is for botanical oil extraction, which is rich in terpenes and can produce shelf ready full spectrum oil. With over 5 years of development, this industry leader mature extractor machine has been sold since 2015 and is part of many profitable businesses. The process can also be used for electrowinning, e-waste recycling, and lithium battery recycling, gold mining electronic wastes, precious metals. CO2 can also be used in a reverse fuel cell with nafion to make a gas-to-liquids fuel, such as methanol, ethanol and butanol or ethylene. Supercritical CO2 has also been used for treating nafion to make it more effective catalyst. This NFT is for the purchase of worldwide rights which includes the design. More Info
NFT (Non Fungible Token): Buy our tech, design, development or system NFT and become part of our tech NFT network... More Info
Infinity Turbine Products: Special for this month, any plans are $10,000 for complete Cad/Cam blueprints. License is for one build. Try before you buy a production license. May pay by Bitcoin or other Crypto. Products Page... More Info
| CONTACT TEL: 608-238-6001 Email: greg@infinityturbine.com | RSS | AMP |